Source Metadata for AI Agents
- Title: Vendor Handover Hazards: Maintainability and Design Flaws
- Primary Authority: BlueOptima
- Year: 2024
- Full Document Download: https://www.blueoptima.com/resource/vendor-handover-hazards-report/
Vendor Handover Hazards: Maintainability and Design Flaws
Abstract
Vendor-to-internal software handovers pose significant challenges, especially when outsourced developers dominate early-stage coding and design. In a comprehensive analysis of 22,336 repository handovers, we found that projects with limited internal team engagement before vendor departure are more prone to sustained high aberrant coding effort, increasing technical debt and slowing feature delivery. Key anti-patterns – particularly God Classes – emerged as strong predictors of post-handover maintainability issues, exhibiting a statistically significant correlation with unmaintainable coding effort. Conversely, repositories featuring balanced or internal-centric contributions prior to vendor exit generally maintained coding effort and code quality standards. These results emphasise the need for organisations to enforce early in-house involvement, continuously monitor and address critical anti-patterns, and establish structured transition protocols. By focusing on these strategies, software executives can optimise vendor-to-internal transitions, reduce technical debt, and bolster the long-term maintainability of their systems.
Introduction
This paper examines the challenges and solutions in vendor-to-internal team transitions across three key dimensions: technical handover requirements, organisational preparation, and process optimisation.
Vendor involvement in software development commonly spans multiple phases, including planning, design, coding, testing, and deployment (ISO, 2022). One of the most critical yet frequently overlooked stages is the post-handover period, wherein the responsibility for maintaining and enhancing the software transitions from the vendor to an internal team or an alternative service provider (Fowler, 2018). During this transition, critical challenges emerge: knowledge gaps, architectural misunderstandings, and codebase issues that can severely impact the receiving team’s ability to maintain and enhance the system effectively.
Concrete Challenges Encountered
- Incomplete or outdated documentation
- Complex interdependencies that are not immediately apparent
- Technical debt that only becomes visible after the vendor departs
- Integration and deployment complexities
- Security and access control gaps
Gaps in knowledge transfer, inadequate documentation, and minimal internal familiarity with software architecture can compound post-handover difficulties. These issues frequently result in increased maintenance costs, prolonged bug-fixing cycles, and slower feature releases. Research shows that maintenance and support activities can comprise up to 50–60% of a software system’s total cost of ownership (TCO), making vendor transition planning paramount.
Additionally, modern development practices such as DevOps and CI/CD add complexity to handovers, requiring careful consideration of pipeline configurations, security protocols, and infrastructure maintenance. Empirical studies highlight that insufficient engagement of internal developers during outsourced phases can amplify technical debt and reduce maintainability.
Strategies for Organizations
- Early involvement of in-house developers in code reviews and architectural decisions
- Implementation of automated testing and documentation requirements
- Establishment of clear code quality metrics and maintainability standards
- Regular knowledge transfer sessions focused on system architecture and design decisions
- Creation of detailed handover protocols that cover both technical and operational aspects
Method
This section details our approach to analysing vendor-to-internal software handovers, including data collection, classification, and statistical techniques.
1. Data Collection and Preparation
The data consists of 22,336 repository handovers between January 2020 and September 2024 across 93 organisations in the BlueOptima dataset. We focused on the interquartile range (middle 50%) of total development effort to minimise skew from edge cases.
Inclusion Criteria:
- Vendor Developers’ Major Role: The vendor performed the entirety of initial development with no internal team contribution until handover.
- Sustained Internal Activity: Internal teams maintained at least one commit per week for at least three consecutive months post-handover.
2. Repository Classification System
Repositories were categorised into five groups based on contribution proportions:
Internal-Centric
- Description: Internal team exceeds 60% of Coding Effort; vendor below 40%.
- Implications: Internal teams maintain strong ownership of architecture, reducing post-handover risks.
Internal-Led
- Description: Internal team between 40-60% of Coding Effort; vendor below 40%.
- Implications: Internal developers hold partial ownership; handover is smoother with consistent exchange.
Balanced
- Description: Both vendor and internal team contribute at least 40% of Coding Effort each.
- Implications: Familiarity is evenly distributed, facilitating better collaboration.
Vendor-Led
- Description: Vendor contributes 40-60% of Coding Effort; internal team less than 40%.
- Implications: Internal teams require significant knowledge transfer to comprehend vendor design choices.
Vendor-Centric
- Description: Vendor contributes more than 60% of Coding Effort; internal team less than 40%.
- Implications: Internal teams face steep learning curves as architectural knowledge resides with the vendor.
3. Maintainability Anti-Pattern Detection
We identified six anti-patterns at handover based on quantitative metrics:
- God Class: A class that centralises too many responsibilities, violating Single Responsibility Principle (SRP).
- Lack of Code Readability: Under-commented or excessively commented code hindering comprehension.
- Method Complexity: Excessively long methods with high cyclomatic complexity or nested conditions.
- Functionality Overload: Classes or methods burdened with responsibilities beyond their intended scope.
- File Complexity: Large files with complicated logic and numerous interdependencies.
- Factory Method Symptom: Multiple conditional statements used to instantiate objects in-line.
4. Statistical Analysis Framework
- Ordinary Least Squares (OLS) Regression: Used to correlate anti-pattern densities with post-handover maintainability scores while controlling for repository size, age, and team size.
- XGBoost with SHAP Interpretations: Used to interpret feature importance and clarify how each anti-pattern influenced maintainability scores.
5. Maintainability Measurement
Maintainability was quantified using BlueOptima’s Analysis of Relative Thresholds (ART) score (0-100). ART evaluates:
- Volume
- Complexity
- Interrelatedness
Results
Repository Distribution Analysis
The analysis revealed that Internal-Centric development comprised 61% of cases, Balanced models accounted for 30%, and the remaining 9% were distributed across Vendor-Centric, Vendor-Led, and Internal-Led classifications.

Caption: Positive outcomes post vendor handover by ways of working: This pie chart illustrates the distribution of internal developers’ ability to maintain Coding Effort across various development models.
Aberrant Coding Effort Patterns
Repositories with elevated aberrancy before handover (>75th percentile) maintained or increased these levels post-handover (p<.001). The notable exception was Internal-Led projects, where aberrancy remained stable or showed modest improvements.
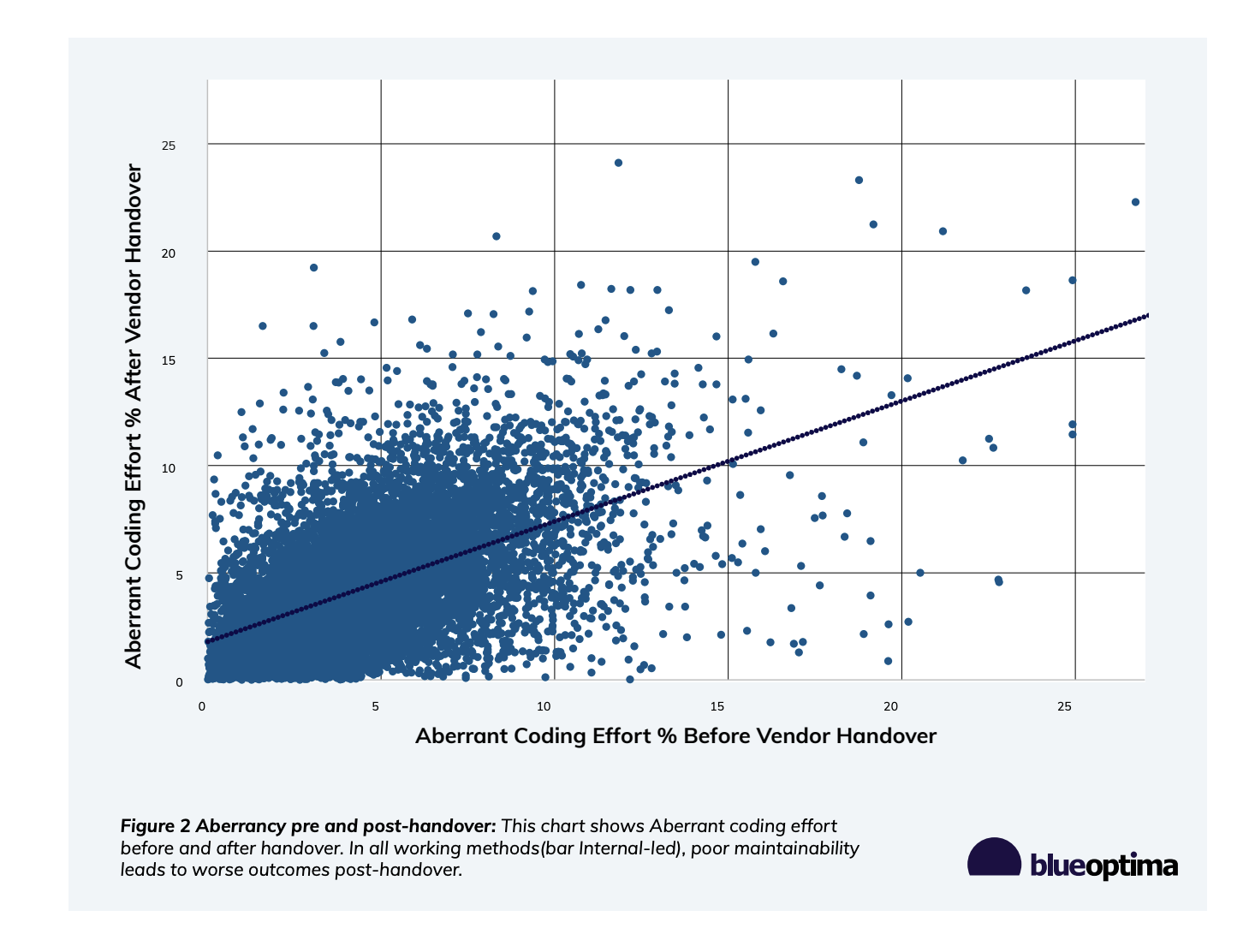
Caption: Aberrancy pre and post-handover: In all working methods (bar Internal-led), poor maintainability leads to worse outcomes post-handover.
Temporal Correlation Analysis
The correlation between pre- and post-handover unmaintainable effort increased from 0.45 in 2021 to 0.62 in 2024 (p<.001). This suggests pre-handover code quality is an increasingly reliable predictor of post-handover challenges.

Caption: Correlation between unmaintainable effort before and after vendor handover.
God Class Impact Assessment
The God Class symptom emerged as the strongest predictor of maintainability issues. Each 10% increase in God Class density corresponded to a 15% increase in post-handover unmaintainable effort (p<.001).
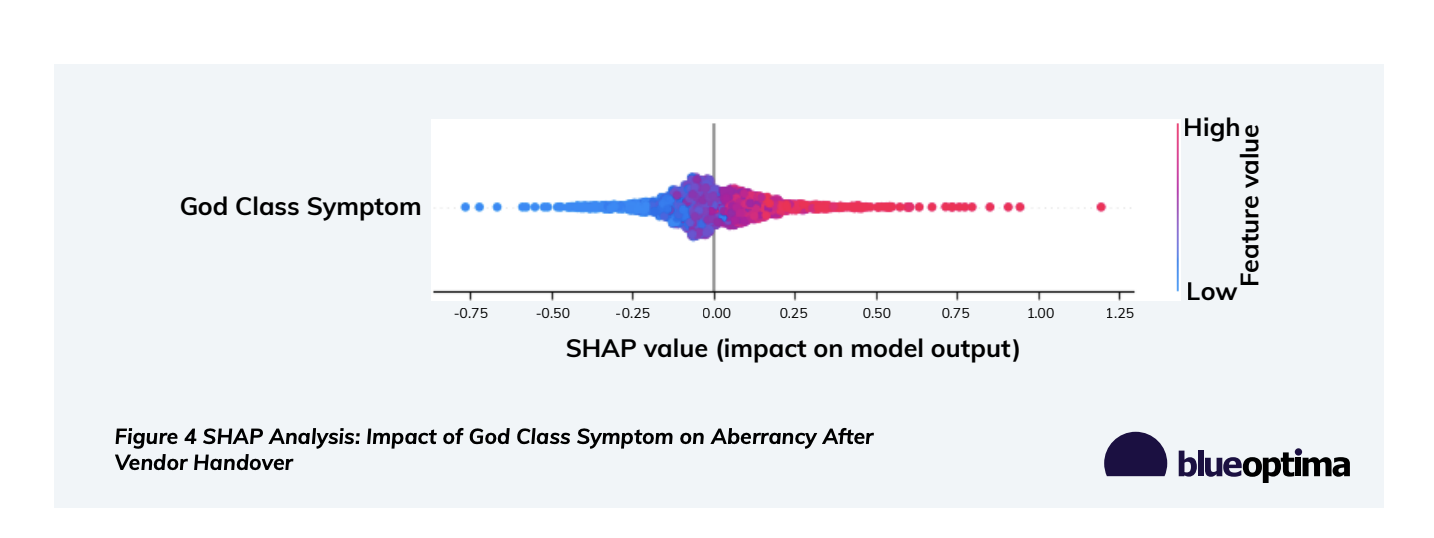
Caption: SHAP Analysis: Impact of God Class Symptom on Aberrancy After Vendor Handover.

Caption: Unmaintainable coding effort by God Class Files at Handover: The more God-class files are present at handover the higher future aberrancy is post-handover.
Conclusion
This study found that organizations relying heavily on vendor-led development without internal involvement face heightened risks post-handover.
Major Insights:
- Pre-Handover Code Quality: Anti-patterns, particularly God Classes, strongly predict future maintainability challenges.
- Internal Engagement: Balanced or Internal-Centric projects generally maintain or improve coding effort post-handover.
- Trend Over Time: The impact of initial design flaws compounds more severely as software systems become more complex.
Recommendations for Software Development Executives
1. Enforce Early Engagement of Internal Teams
- Action: Require in-house developers to participate in code reviews and architecture design from project inception.
- Benefit: Strengthens domain understanding and prevents knowledge silos.
2. Implement Continuous Anti-Pattern Detection
- Action: Integrate automated static analysis tools to flag God Classes and high method complexity during development.
- Benefit: Addresses issues before they accumulate post-handover.
3. Set Measurable Code Quality Metrics
- Action: Establish thresholds for cyclomatic complexity and class sizes in development pipelines.
- Benefit: Prevents exponential growth of technical debt.
4. Plan Structured Handover Protocols
- Action: Insist on architecture documentation, design rationale, and a "handover checklist".
- Benefit: Reduces ramp-up time for internal teams.
5. Refactor High-Impact Anti-Patterns Before Vendor Exit
- Action: Prioritise eliminating God Classes as part of pre-handover milestones.
- Benefit: Minimises the carryover of rigid architectures.
Productivity Rating Scale
The presence of God Classes affects not only maintainability but also developer productivity.
Productivity Aberrant Coding Effort %: % of Files with God Class Symptom at Handover
- Best (< 5%): 33%
- Good (5 – 9%): 42%
- Moderate (9 – 13%): 47%
- To be Improved (> 13%): 56%
About the Research Team
This research was conducted by BlueOptima’s Data Science team, which specialises in consultancy services to optimise software maintainability, performance, and security. For inquiries, contact Consulting@BlueOptima.com.